Table of Contents
Creating a personal VPN on a Virtual Private Server (VPS) is a practical way to gain privacy, bypass geographic restrictions, and protect data on public Wi‑Fi. By the end of this article you will understand the full workflow—selecting a reliable VPS, installing and configuring OpenVPN, and keeping the service secure.
In this narrative we’ll follow the journey of a typical user who wants more control over their internet traffic. The story starts with research, moves through hands‑on server setup, and finishes with real‑world testing. Along the way, we’ll highlight common pitfalls and best practices, making the process clear even for readers with limited Linux experience.
Before diving into technical details, remember that a VPN does not replace a comprehensive security strategy. It adds a layer of encryption and anonymity, but strong passwords, regular updates, and cautious browsing remain essential.
Choosing the Right VPS Provider

The foundation of a stable VPN is a dependable VPS. Not all providers are equal, and the choice can affect latency, bandwidth, and uptime. Consider the following criteria:
- Location: Choose a data center close to your primary use case to reduce latency.
- Network Bandwidth: Look for providers offering at least 100 Mbps unmetered traffic.
- Operating System Options: Ubuntu LTS releases are widely supported for OpenVPN.
- Pricing and Billing Flexibility: Monthly plans give you the ability to test the service before committing long‑term.
Recommended VPS Features
For a personal VPN, a basic plan with 1 CPU core, 1 GB RAM, and 20 GB SSD storage is sufficient. These specs can handle dozens of simultaneous connections without noticeable slowdown.
Preparing the Server Environment
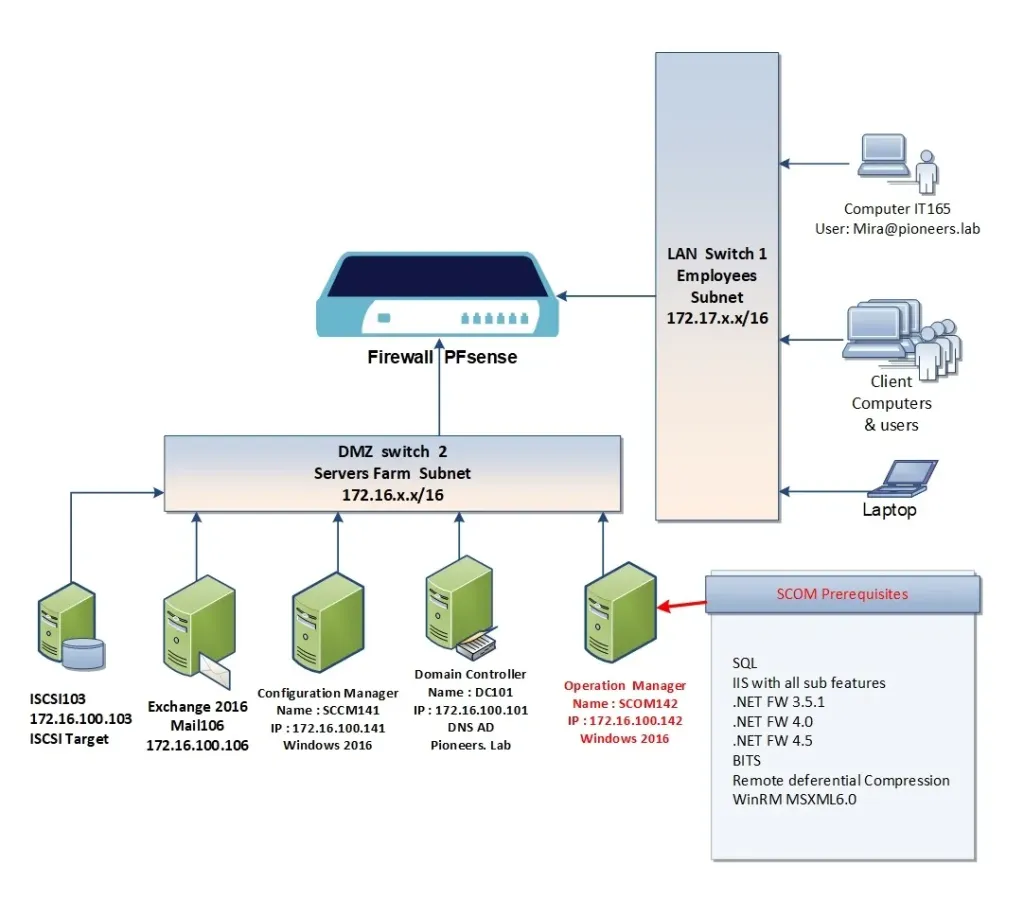
Once the VPS is provisioned, the next step is to secure the environment before installing any software. Begin by connecting via SSH:
ssh root@your_vps_ipAfter logging in, perform the following actions:
- Update the package index and upgrade existing packages:
apt update && apt upgrade -y - Create a non‑root user for day‑to‑day operations:
adduser vpnuser usermod -aG sudo vpnuser - Set up a basic firewall using
ufw:ufw allow OpenSSH ufw enable
These steps create a clean, auditable baseline and reduce the attack surface before the VPN software is installed.
Installing OpenVPN
OpenVPN remains one of the most flexible and widely supported VPN solutions. Its open‑source nature ensures transparency, while its mature ecosystem offers robust documentation.
To install OpenVPN on Ubuntu, you can use the official script provided by Nyr, which automates most of the configuration:
apt install -y wget curl
wget https://git.io/vpn -O openvpn-install.sh
chmod +x openvpn-install.sh
./openvpn-install.shThe script will prompt you for:
- Preferred protocol (UDP is faster for most uses, TCP offers better reliability over restrictive networks).
- Port number (default 1194, but you can choose an alternative to avoid blocking).
- DNS provider (Google, Cloudflare, or a custom DNS for privacy).
After answering the prompts, the script generates a client configuration file (.ovpn) and places it in /root. You can retrieve it with scp:
scp root@your_vps_ip:/root/client.ovpn ./client.ovpnWhy Use a Script?
The script abstracts complex steps such as generating certificates with Easy‑RSA, configuring server directives, and setting up IP forwarding. This reduces the risk of misconfiguration and speeds up deployment.
Configuring Server and Client Files
Even though the script does most of the heavy lifting, you may need to tweak the configuration for specific use cases. Common adjustments include:
- Enabling IPv6 support: Add
push "redirect-gateway ipv6"to the server config. - Restricting client access: Use the
client-config-dirdirective to define per‑client rules. - Custom DNS: Insert
push "dhcp-option DNS 1.1.1.1"for Cloudflare DNS.
Open the server configuration file located at /etc/openvpn/server.conf with your preferred editor, apply the changes, and restart the service:
systemctl restart openvpn@serverOn the client side, import the .ovpn file into any OpenVPN client—Windows, macOS, Android, or iOS—and connect. The client automatically pulls the necessary routes and DNS settings from the server.
Setting Up Firewall and Routing
To allow VPN traffic through the VPS firewall, you must open the chosen port and enable packet forwarding. With ufw, execute:
ufw allow 1194/udp
ufw allow 1194/tcp # if you selected TCP
ufw reloadEnable IP forwarding permanently by editing /etc/sysctl.conf:
net.ipv4.ip_forward=1
net.ipv6.conf.all.forwarding=1Apply the changes with sysctl -p. Finally, configure NAT so that client traffic is masqueraded to the VPS public IP:
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
iptables-save > /etc/iptables.rulesPersist the rules across reboots by adding a small systemd service or placing the commands in /etc/rc.local.
Testing the Connection
Before trusting the VPN for everyday use, perform thorough testing:
- IP Leak Test: Visit ipleak.net while connected. The displayed IP should be the VPS’s address.
- DNS Leak Test: Verify that DNS queries resolve through the configured DNS provider, not your ISP.
- Speed Test: Use
speedtest-clion both the server and client to compare latency and throughput. - Routing Check: Run
tracerouteto a remote host and confirm that the first hop is the VPS.
If any of these checks reveal leaks or performance issues, revisit the server configuration, firewall rules, and DNS settings.
Maintaining and Updating Your VPN
Like any network service, a VPN requires regular maintenance. Follow these practices to keep the tunnel secure and reliable:
- Patch the OS: Schedule weekly
apt update && apt upgrade -yruns. - Rotate Certificates: Use the script’s “revoke” option to invalidate old client certificates and generate new ones.
- Monitor Logs: Check
/var/log/openvpn.logfor unusual connection attempts. - Backup Configurations: Store
server.confand theeasy-rsaPKI directory in a secure off‑site location. - Scale as Needed: If you anticipate more concurrent users, upgrade the VPS CPU, RAM, or consider load‑balancing multiple servers.
For a deeper dive into server automation, you might explore scripts that integrate with continuous deployment pipelines. Such tools can provision a fresh VPN instance with a single command, ensuring consistency across environments.
By following these steps, you now possess a fully functional, self‑hosted VPN that you control end‑to‑end. The flexibility of a VPS allows you to adjust settings, add additional protocols like WireGuard, or even host other privacy‑focused services such as a DNS-over-HTTPS resolver.
In summary, building a personal VPN on a VPS blends technical rigor with practical benefits. The process demystifies networking concepts, encourages disciplined security habits, and ultimately gives you the freedom to browse the internet on your own terms.